
Instructions for the information security change tool
The change request tool is intended to serve as the primary tool for processing normal change requests related to an information security connection.
Specify the order delivery time, according to which the request is fulfilled. The requests are fulfilled according to the selected delivery time. “Next business day” means that the request is fulfilled by 4:00 pm on the next business day. “Timed” means that the change can be made at a desired point in time, however no sooner than after at least two weekdays. “Express” means that the request is fulfilled within two hours of being submitted. “8h (24/7)” means that the request is fulfilled within eight hours from being submitted. * marked fields are mandatory fields
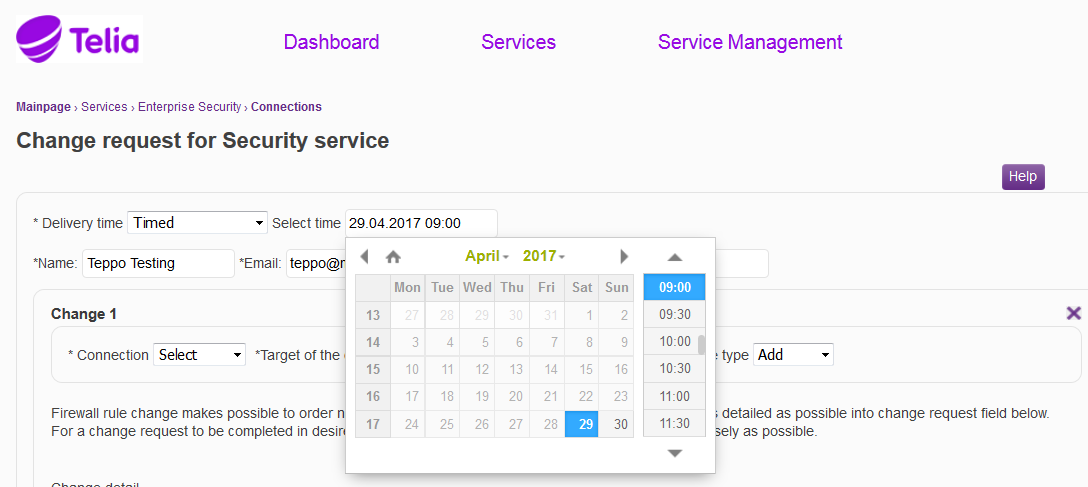
Figure: Specifying the delivery time
The requester’s details are specified in the ‘Name’, ‘Email’ and ‘Phone’ fileds, and they are received automatically from the user details. These details can be changed, if information on the change is to be delivered to another person than the requester.

Figure: Specifying the requester’s details
The connection to which the change is to be made is specified in the ‘Connection’ menu. The service to which the change is to be made is selected in the ‘Target of the change’ menu. The ‘Target of the change’ menu shows only the services specified for the information security connection in question. All change targets of the connection are not shown with all delivery methods, e.g. a LAN-TO-LAN VPN order is not available as an express order. There are separate instructions for the change targets. In the ‘Change type’ menu it is specified whether the request relates to an addition, change or deletion. The firewall rules can be seen by web-browser, instructions are available here. Security rule application instructions

Figure: Specifying the connection, the target of the change, and the change type
In the ‘Change details’ field, the change requested is specified. The obligatory information required in order for the request to be fulfilled is requested in the ‘Change details’ field. The obligatory information on the target of the change is pre-filled in the ‘Change details’ field. Filling in this information ensures that the request can be fulfilled. If information is missing from the ‘Change details’ field, our specialist has to take actions to look for it. If the order is defective, we cannot guarantee that the delivery takes place within the estimated delivery time.

Figure: Specifying the change
After the change has been specified, it is possible to add changes to the request by clicking "Add change". The request can be submitted by clicking “Send request”. Under “Add”, select “Save request” or “Cancel request”. Under “Add”, it is also possible to cancel a request that has already been sent, if the processing of the request has not yet been started by selecting “Return request”. Attachments can be added to the request by clicking “Add attachments”.

Figure: Adding changes, sending the request, adding attachments, and specifying other functions
When the request has been fulfilled, the user specified in the request receives an acknowledgement to this end by email. Telia can return the request if more information is required and Telia has been unable to reach the requester by phone. A notification is also sent to the requester’s email on a returned request.
Different change targets can be found in the table, and if you select a target, you can see a more detailed general description of the service, the issues to be specified and the order instructions.
Subjects of change
3 Network address translation (NAT)
7 Antivirus protection, Advanced Threat Protection and Anti-Spyware
1 Firewall
rule change
Firewall rules filter traffic between two data communications networks, for example the company’s LAN or subscriber line and the Internet, as specified in the firewall rules.
With firewall rule changes, you can request new rules, changes to the existing rules or their deletion.
1.1 Rule request
Below, you will find a picture of a firewall rule base and descriptions of the settings that can be ordered by a firewall rule request.

Figure. Firewall rule.
Definition of rule number
The rule number is the point in the rule base where the rule is read. The firewall checks the rule base against the connection details in sequential order and stops when it finds a match. For this reason, the rule numbers are important.
Definition of rule name (Name)
Give a name to the rule. The name will remain unchanged in the rule base. The name of the rule has no bearing on its function, but individual names make it easier to refer to rules when making changes to them. Unlike rule numbers, the names of rules do not change when new rules are added.
Definition of rule type (Type)
Define the rule’s type. The rule type defines how traffic between different zones functions. The available alternatives are:
· Intrazone: traffic inside the same zone
· Interzone: traffic between defined zones
· Universal: traffic between all zones specified in the rules
Definition of source zone (Zone)
Specify the rule’s source zone, i.e. the zone from which the traffic arrives to the firewall.
Definition of source address (Address)
Specify the source address or addresses to be used. The addresses can be individual IP addresses, IP network addresses or object groups including several IP addresses, networks or groups. Geographical protection can also be specified in the Source Address field.
Definition of source user (User)
Specify users, user groups, devices or device groups obtained from user directories can be used if the customer has ordered the supplementary user identification service.
Definition of destination zone (Zone)
Specify the destination zone for the rule, i.e. the destination zone of the traffic.
Definition of destination address (Address)
Application definition (Applications)
Specify the applications permitted by the rule. A more detailed list can be found at https://applipedia.paloaltonetworks.com/ or under firewall management. Application user messages are defined separately according to the instructions available here.
Service and URL category definition (Service)
The TCP/UDP port(s), service(s) and group(s) to be used are specified in the service. The web categories used for the rule are specified in the URL category. The web categories can be found at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the table found in the web content filtering instructions.
Definition of action (Action)
The action is specified using one of the following options:
- Allow, i.e. permit the traffic.
- Deny, i.e. reject the traffic.
This differs from Drop in that the firewall informs the party attempting
to establish a connection about the disconnection. The use of Deny is only
recommended in special cases.
- Drop, i.e. block the traffic.
Profile definition (Profile)
Define profiles if the rule will include antivirus, advanced threat protection, intrusion prevention or web content filtering functionalities. The functionalities are described in more detail in their own sections.
Rule tracking (Options)
Specify whether or not a log will be kept of connections that activate the rule.
Requesting a rule and sending it to implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample rule request
Rule number: 1
Rule name: Internet traffic
Rule type: Interzone
Source zone: Intra
Source address: Intra_1.1.1.0m0
Source user: -
Destination zone: Untrust
Destination address: Any
Application: Any
Service: http, https
Action: Allow
Profile: Antivirus, Anti-Spyware, Intrusion Prevention, Web Content Filtering
Track: No
1.2 Rule change request
Specify the rule to be changed and the change to be made. A rule change request should include the name or at least the number of the rule to be changed.
Sample change request
Rule number: 1
Rule name: Internet traffic
Change to be made: Add the network Intra_1.1.2.0m0 to the source addresses.
1.3 Rule deletion request
Specify the rule to be deleted. A rule deletion request should include the name or at least the number of the rule to be deleted.
Sample deletion request
Rule to be deleted: Number 1
Name of the rule to be deleted: Internet traffic
Return to the selection Subjects of change.
1.4 Application control user message
request
The functionality can be used to inform the users in real time of the limitations of application usage, risks of the Internet, and the security policy of the organisation. The figure below presents the Block user message of content filtering, along with descriptions of the specifications required for requesting the message for application management.

Figure. Application control Block message.
Message name
Give a name to the message.
Message content
Specify the content of the message. The content can include the user’s name/IP address and the application being used.
Saving a rule and sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample rule request
Message name: Application control Block message
Message content: Access to the application you were trying to use has been blocked in accordance with company policy. Please contact your system administrator if you believe this is in error.
1.5 Application control user message change request
Specify the profile to be changed and the change to be made.
Sample change request
Message name: Application control Block message
Message content: Access to the application you were trying to use has been blocked in accordance with company policy. Please contact your system administrator if you believe this is in error.
Change to be made: Change the user message logo. The logo is in the file attached to the request.
1.6 Application control user message deletion request
Specify the user message to be deleted.
Sample deletion request
Name of the message to be deleted: Application control Block message
Return to the selection Subjects of change.
2
Object
change
Objects are used when the rule base of a firewall is specified. The object can be an address, network, user, group, user group, service or service group.
With a firewall object change, you can order new objects, changes to existing objects and the deletion of objects.
You must assign a name for each new object. The name should indicate the type, context and content of the object. In addition, further information on each new object can be provided in the Description field.
The objects that can be modified are described below:
Host
A host object contains a single IP address. The address (IP address, e.g. 192.168.1.1) or 2001:db8:85a3::8a2e:370:7334 for IPv6.

Figure. Host object.
Network
A network object includes an entire network and its masks. Address (IP address, e.g. 192.168.1.0 or 2001:db8:85a3::8a2e:370:7334 for IPv6). Mask (network mask, e.g. 255.255.255.0 or 120 for IPv6).

Figure. Network object.
IP Range
An IP range object includes a range of IP addresses, e.g.192.168.1.1 – 192.168.1.10 or 2001:db8:85a3::8a2e:370:7334 – 2001:db8:85a3::8a2e:370:7340 for IPv6.

Figure. IP range object
Service
A service object includes the protocol and the port. Protocol, e.g.TCP/IP, UDP, http. Port, e.g. tcp888.

Figure. Service object
Object and service group
An object and service group includes a number of other objects. Thus, an object group may contain hosts, networks, IP ranges and object groups. An object group can only include objects of the same IP version.
For example, the group Intra_verkot contains IP addresses and includes the objects yritys_10.10.10.10 and yritys_10.10.20.0m0.

Figure. Group object
A service group can include services and service groups. For example, the group Intra_Palvelimen_portit contains service groups and includes the ports tcp 400–402 and tcp 8001.

Figure. Service group object
2.1 Object request
Definition of object type
Specify whether the request concerns a host, user, network, service or group object.
Definition of object name
Specify a name for the object.
Definition of object content
Specify what the object includes (IP addresses, networks, etc.).
Definition of object comment
Enter a comment on the object if required.
Requesting an object and sending it to implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample request for a new object
Definition of object type: Host object
Definition of object name: Intra_1.1.1.1
Definition of object content: 1.1.1.1
Definition of object comment: Intranet server
2.2 Object change request
Specify which object is to be changed (name) and the change to be made.
Sample object change request
Name of the object to be changed: Intra_1.1.1.1
New name for the object: Intra_1.1.1.3
New content for the object: 1.1.1.3
New comment for the object: do not change the comment
2.3 Object deletion request
Specify the object to be deleted (name). Please note that the object in question will be deleted from the information security device.
Sample object deletion request
Name of the object to be deleted: Intra_1.1.1.1.
Return to the selection Subjects of change.
3
Network
address translation (NAT)
NAT rules specify which addresses or services will be translated to which addresses or services. As a rule, the NAT function is used to create a dynamic Hide NAT service for private addresses in the Intranet, used for Internet traffic.
The original source and destination address and service must be specified. If the traffic meets these criteria, the changes specified in the following fields will be carried out, i.e. the source or destination address will be translated.
A NAT request can be used to order new network address translations, changes to them or their deletion.
Please note: The rules of firewalls and other security services uses the original, untranslated IP addresses.
3.1 NAT rule request
The figure below presents a NAT rule and descriptions of the settings ordered with a NAT request.
![]()
Figure. NAT rule.
Definition of rule number (No)
The rule number is the point in the rule base where the rule is read. The firewall checks the rule base against the connection details in sequential order and stops when it finds a match. For this reason, the rule numbers are important.
Definition of rule name (Name)
Rule name. The name will remain unchanged in the rule base.
Definition of original source zone (Source Zone)
Specify the original source zone.
Definition of original destination zone (Destination Zone)
Specify the original destination zone.
Definition of original destination interface (Destination Interface)
Specify the original destination interface.
Definition of original source address (Source Address)
Specify the original source address used. It can be an individual IP address, an IP network, or an object group including several IP addresses, IP networks or groups.
Definition of original destination address (Destination Address)
Specify the original destination address used. It can be an individual IP address, an IP network or an object group including several IP addresses, networks or groups.
Definition of original service (Service)
The TCP/UDP port, service or group to be used are specified in the service.
Definition of translated source address (Source Translation)
Specify the translated source address. It can be an individual IP address, an IP network, or an object group including several IP addresses, IP networks or groups.
Definition of translated destination address (Destination Translation)
The translated destination address. It can be an individual IP address, an IP network or an object group including several IP addresses, networks or groups.
Saving a rule and sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample rule request, translation of one network address
Rule number: 1
Rule name: DMZ server address translation
Original source zone: Trust
Original destination zone: Internet
Original interface: Any
Original source address: Yritys_10.10.10.10
Original destination address: Any
Original service: Any
Translated source address: Yritys_172.2.1.1
Translated destination address: Any
Sample rule request, translation of several network addresses to a single address (Hide-nat)
Rule number: 1
Rule name: Internet traffic
Original source zone: Trust
Original destination zone: Internet
Original interface: Any
Original source address: Yritys_10.10.10.0m0
Original destination address: Any
Original service: Any
Translated source address: Yritys_172.2.1.1
Translated destination address: Any
3.2 NAT rule change request
Specify the rule to be changed and the change to be made.
Sample change request
Rule number: 1
Rule name: Internet traffic
Change to be made: Replace the original source address by the network Yritys_10.10.11.0m0.
3.3 NAT rule deletion request
Specify the NAT rule to be deleted.
Sample deletion request
Rule to be deleted: Number 1
Rule name: DMZ server address translation
Original source zone: Trust
Original destination zone: Untrust
Original interface: Any
Original source address: Yritys_10.10.10.10
Original destination address: Any
Original service: Any
Translated source address: Yritys_172.2.1.1
Translated destination address: Any
Return to the selection Subjects of change.
4
LAN-to-LAN
VPN
The LAN-to-LAN VPN functionality allows strongly encrypted IPSec VPN connections to be set up between the customer’s offices or partners.
With a LAN-to-LAN VPN change request, you can order new VPN connections or changes to existing VPN connections or their removal. If the firewall supports IPv6 addresses, you can also specify a new IPv6 VPN. You cannot mix different IP versions in the same VPN; all addresses and objects must use the same IP version. To allow the VPN connection to be implemented, a LAN-to-LAN VPN change request must include the following information:
- General VPN details, such as
the requested delivery time and the contact details of the other party.
The information specified in the LAN-to-LAN VPN change
request will be sent to the e-mail address of the other party’s contact
person.
- VPN parameters.
- Internal and external IP
addresses, i.e. the networks that operate on the VPN connection and whose
traffic will be encrypted.
- Further details concerning the
order, such as the services/ports activated for the connection.
4.1 LAN-to-LAN VPN connection order
Definition of general details
Specify the details of the other party of the VPN connection here. This information will be needed for the specification of the VPN connection. The following information is required:
· Company name (if external company)
· Technical contact person performing the configuration at the other end
· E-mail address of technical contact person
· Mobile phone number of the technical contact person (a pre-shared secret password will be sent to this number).
Definition of VPN parameters
· Name of VPN connection
· Starting point of VPN connection
· End point of VPN connection
· Mode. The options are Main and Aggressive. ‘Main’ refers to normal negotiation complying with the IPSEC standard in the setting up of the connection, while ‘Aggressive’ overrides certain phases to speed up the negotiation.
· Phase1 Diffie-Hellman group. This protocol protects the PKI key exchange.
· Phase1 Encryption Algorithm. Phase 1 encryption algorithm for encrypting a phase 2 negotiation.
· Phase1 Hash Algorithm. Phase 1 Hash Algorithm secures the integrity of phase 2 negotiations (using a secure hash).
· Phase1 Lifetime seconds. The duration of phase 1 in seconds. Phase 1 is (automatically) renegotiated after the time is up.
· Phase2 Perfect Forward Secrecy. Improves data security in the event that the PKI key of the VPN connection is found out by means of wiretapping.
· Phase2 Lifetime seconds. The duration of phase 2 in seconds. Phase 2 is (automatically) renegotiated after the time is up.
· Phase2 ESP/AH. ESP (Encapsulated Security Payload) encrypts the package. AH (Authentication Header) only checks the integrity of the package.
· Phase2 Encryption Algorithm. Phase 2 encryption algorithm for traffic encryption.
· Phase2 Authentication Algorithm. Phase 2 Hash Algorithm secures the integrity of phase 2 traffic (using a secure hash).
Please note: The VPN parameters of the connected VPN devices must be completely identical, and not all devices support all options offered by the tool. The change tool will propose common compatible parameters recommended for use.
Definition of internal addresses
Specify the internal IP addresses, with their network masks, that will operate on the requested VPN connection. You can specify several networks. Specifying hosts (individual IP) is not recommended. Firewall rules can be used to specify in more detail the IP addresses, protocols or ports that are allowed to operate within the VPN connection.
Definition of external addresses
Specify the networks that will operate on the requested VPN connection from the other party’s VPN device.
Definition of further information
Specify further information related to the request. Entering the activations related to the VPN connection, i.e. the protocols that will be allowed for the connection, is also recommended. If necessary, the rules can also be ordered separately with a firewall rule change request.
Sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample VPN change request
Contact details of the other party in the VPN connection
Company name: Company Oy
Name of the technical contact person: Ted Tester
E-mail address of the technical contact person: ted.tester@company.fi
Mobile phone number of the technical contact person: +358 40 123 4567
Definition of VPN connection parameters
Name of the VPN connection: VPN-to-Partner
Starting point of VPN connection: 192.168.1.1
End point of VPN connection: 192.168.2.1
Mode (default main): main
Phase1 Diffie-Hellman group (default group2): group2
Phase1 Encryption Algorithm (default aes256): aes256
Phase1 Hash Algorithm (default sha-1): sha1
Phase1 Lifetime seconds (default 28000): 28000
Phase2 Perfect Forward Secrecy (default no-pfs): no-pfs
Phase2 Lifetime seconds (default 3600): 3600
Phase2 ESP/AH (default esp): esp
Phase2 Encryption Algorithm (default aes256): aes256
Phase2 Authentication Algorithm (default sha-1): sha1
Networks allowed on the VPN connection
Internal addresses: 10.10.10.0m0
External addresses: 20.20.20.0m0
Further details on the request: VPN-connection-related rules for the firewall which will allow all traffic.
4.2 LAN-to-LAN VPN connection change request
Specify the VPN connection to be changed and the change to be made.
Sample change request
Name of the VPN connection: VPN-to-Partner
Change to be made: Adding network 10.10.20.0m0 as the internal address.
4.3 LAN-to-LAN VPN connection deletion request
Specify the VPN connection to be deleted.
Sample deletion request
Delete the following VPN connection.
Name of the VPN connection: VPN-to-Partner
Return to the selection Subjects of change.
5
Routing
Dynamic routing (BGP) or static routing is used for routing the firewall through the network interfaces of the internal network. In dynamic routing, the route data is thus received by the firewall and no configuration changes will be required if the dynamic routing has been specified. In static routing, the network and interface through which the network is advertised must be specified for the firewall.
A routing change request can be used to order new internal networks to be added to the firewall, changes to existing internal networks or the deletion of internal networks.
5.1 Routing request
Definition of IP version
Specify the IP version used.
Definition of IP address and mask
Specify the internal network’s IP network address and mask.
Definition of zone
Specify the zone to which the network will be added.
Definition of network interface to be routed
Specify the network interface of the internal network from which the network is advertised.
Sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample routing request
Network address and mask to be routed: 10.10.10.0m0
Zone: Intra
Network interface of the route: eth1
5.2 Routing change request
Specify the route to be changed and the change to be made.
Sample change request
Network address and mask to be routed: 10.10.10.0m0
Zone: Intra
Network interface of the route: eth1
Change to be made: Change the network interface of the route to eth2.
5.3 Routing deletion request
Specify the route to be deleted.
Sample deletion request
Delete the following routing:
Network address and mask to be routed: 10.10.10.0m0
Zone: Intra
Network interface of the route: eth1
Return to the selection Subjects of change.
6 Web
filtering
A web filtering order can be used to order new rules for the web content filtering service, changes to the rules or the deletion of rules from the service.
In web content filtering, the URL (Uniform Resource Locator) of a downloaded Internet page is compared with a database where web pages are pre-categorised into certain page categories. This functionality allows users to be informed in real time of web traffic restrictions, the risks of the Internet, and the information security policy of the organisation.
Changes can be made to the scanned networks or users, destination addresses, category, functionality and tracking.
6.1 Web filtering rule request
The figure below presents the default rule for web content filtering and descriptions of the settings that are ordered with a web content filtering request.

Figure. Web content filtering rule.
Definition of profile name (Name)
Specify a name for the profile. The profile name will be used in the profile definition of the rule base policy.
Definition of blocked addresses (Block List)
Specify the addresses that will be blocked.
Definition of action towards blocked addresses (Action for Block List)
Specify an action for traffic from blocked addresses. The available alternatives are:
· Allow (permits traffic)
· Block (stops traffic)
· Alert (logs traffic)
· Continue (requests the user’s approval)
· Override (requests the user to enter a password)
User messages are defined separately according to the instructions available here.
Definition of allowed addresses (Allow List)
Specify the addresses that will be allowed.
Definition of allowed categories (Allow Categories)
Specify the categories that will be allowed. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Definition of categories that will cause an alert to be logged (Alert Categories)
Specify the categories that will be logged. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Definition of blocked categories (Block Categories)
Specify the categories that will be blocked. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Definition of categories requiring confirmation from the user (Continue Categories)
Specify the categories whose traffic requires the user’s approval in the rules (Response Page). All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Definition of password-protected categories requiring confirmation from the user (Override Categories)
Specify the categories whose traffic requires the user to enter a password. All users share the same password. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
The web content filtering categories are listed in the table below.
|
BrightCloud categories |
|||
|
Abortion |
Government |
Motor Vehicles |
Search Engines |
|
Abused Drugs |
Gross |
Music |
Sex Education |
|
Adult and Pornography |
Hacking |
News and Media |
Shareware and Freeware |
|
Alcohol and Tobacco |
Hate and Racism |
Nudity |
Shopping |
|
Auctions |
Health and Medicine |
Online Greeting cards |
Social Network |
|
Bot Nets |
Home and Garden |
Parked Domains |
Society |
|
Business and Economy |
Hunting and Fishing |
Pay to Surf |
Sports |
|
CDNs |
Illegal |
Peer to Peer |
Spyware and Adware |
|
Cheating |
Image and Video Search |
Personal Storage |
Stock Advice and Tools |
|
Computer and Internet Info |
Internet Communications |
Personal sites and Blogs |
Streaming Media |
|
Computer and Internet Security |
Internet Portals |
Philosophy and Political Advocacy |
Swimsuits and Intimate Apparel |
|
Cult and Occult |
Job Search |
Phishing and Other Frauds |
Training and Tools |
|
Dating |
Keyloggers and Monitoring |
Proxy Avoid and Anonymizers |
Translation |
|
Educational Institutions |
Kids |
Questionable |
Travel |
|
Entertainment and Arts |
Legal |
Real Estate |
Violence |
|
Fashion and Beauty |
Local Information |
Recreation and Hobbies |
Weapons |
|
Financial Services |
Malware Sites |
Reference and Research |
Web Advertisements |
|
Gambling |
Marijuana |
Religion |
Web Hosting Sites |
|
Games |
Military |
SPAM URLs |
Web based email |
Figure. Web content filtering categories.
Sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample rule request
Profile name: Web content filtering
Blocked addresses: -
Action for blocked addresses: -
Allowed addresses: www.sonera.fi
Allowed categories: Business and Economy
Logged categories: Hunting and Fishing
Forbidden categories: Abused Drugs
User-approved categories: Gambling
Password-protected categories: Real Estate
6.2 Web filtering rule change request
Specify the rule to be changed and the change to be made.
Sample change request
Profile name: Web content filtering
Blocked addresses:
Action for blocked addresses: -
Allowed addresses: www.sonera.fi
Allowed categories: Business and Economy
Logged categories: Hunting and Fishing
Forbidden categories: Abused Drugs
User-approved categories: Gambling
Password-protected categories: Real Estate
Change to be made: Remove Gambling from the user-approved categories.
6.3 Web filtering rule deletion request
Specify the rule to be deleted.
Sample deletion request:
Delete the following profile
Profile name: Web content filtering
Return to the selection Subjects of change.
6.4 Web filtering user message request
This functionality allows users to be informed in real time of web traffic restrictions, the risks of the Internet, and the security policy of the organisation.
The figures below present the Block and Continue user messages of content filtering, along with descriptions of the specifications required for requesting the web content filtering user message.

Figure. Web content filtering Block message

Figure. Web content filtering Continue message
Message type (Block/Continue/Override)
The message can be either a block, continue or override message. A Block message is sent if the traffic is not allowed. A Continue message requires the user to approve the traffic on the "Response page" (Continue). An Override requires the user to enter a password in the prompt on the "Response page". Only one password can be specified, and all users share the same password.
Message name
Give a name to the message.
Message content
Specify the content of the message. The contents of the message can indicate the user’s name/IP address, the URL address to which a connection attempt is being made and the URL address category.
Saving a rule and sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample rule request
Message type: Block
Message name: Web content filtering Block message
Message content: Access to “web-site” is blocked according to the organisation’s security policy. For more information, please contact your helpdesk.
6.5 Web filtering user message change request
Specify the message to be changed and the change to be made.
Sample change request
Message type: Block
Message name: Web content filtering Block message
Message content: Access to “web-site” is blocked according to the organisation’s security policy. For more information, please contact your helpdesk.
Change to be made: Change the user message logo. The logo is in the file attached to the request.
6.6 Web filtering user message deletion request
Specify the message to be deleted.
Sample deletion request
Name of the message to be deleted: Web content filtering Block message
Return to the selection Subjects of change.
7
Antivirus
protection, Advanced Threat Protection and Anti-Spyware
The antivirus service scans the files downloaded through the firewall and prevents any malware from entering the customer network according to the company’s scanning policy. The antivirus service supports the most common web browsing, data transmission and email protocols. The user receives a user message if any viruses detected. The firewall updates the virus database automatically from the manufacturer’s update servers.
The Advanced Threat Protection service monitors how a file behaves in a workstation environment and attempts to prevent unknown malware from entering the customer network. Specify in the antivirus settings whether unknown files will be scanned or not.
The Anti-Spyware function must also be specified in the antivirus settings. Anti-Spyware detects the downloading of unauthorised programs that send user information and traffic from spyware programs already installed on the computer. Anti-Spyware also identifies known malware domains, blocking Botnet traffic.
With an antivirus request, you can order new profiles for the Antivirus and Advanced Threat Protection services or change or delete such profiles.
7.1 Antivirus and Advanced Threat Protection profile request
In the following, you will find a picture of an antivirus rule and descriptions of the settings requested by an antivirus rule request.

Figure. Antivirus profile.
Definition of profile name (Name)
Specify a name for the profile. The profile name will be used in the policy’s profile definition.
Definition of packet scanning (Packet Capture)
Specify whether or not a packet will be scanned.
Definition of scanned protocols (Name)
Specify which protocols will be scanned. The available alternatives are:
Http, smtp, imap, pop3, ftp, smb or all protocols (any)
Definition of action for scanned protocols (Action)
Specify what action will be taken if a virus is detected in a protocol being scanned. The available alternatives are: Alert, Block (default) and Allow. Actions can be individually specified for each protocol. User messages are defined separately according to the instructions available here.
Definition of Advanced Threat Protection (WildFire Action)
Specify whether or not files will be sent for scanning if their function is not known. The available alternatives are: Yes (default if the service is enabled) or No. Actions can be individually specified for each protocol.
Definition of application exceptions (Name)
Specify an application for which exceptional specifications will be made. The exception will apply to the entire profile.
Definition of action for application exceptions (Action)
Specify the action that will be taken if an application exception is detected. The available alternatives are: Alert, Block and Allow.
Definition of file exceptions (Threat exceptions)
You can use this definition to specify files that will not be scanned.
Sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Example of a profile request
Profile name: Antivirus
Packet scanning: No
Scanned protocols: Any
Action for scanned protocols: Block
Advanced Threat Protection: Yes (for all protocols)
Definition of application exceptions: -
Action for application exceptions: -
Definition of file exceptions: -
7.2 Antivirus and Advanced Threat Protection profile change request
Specify the rule to be changed and the change to be made.
Sample change request
Profile name: Antivirus
Packet scanning: No
Scanned protocols: Any
Action for scanned protocols: Block
Advanced Threat Protection: Yes (for all protocols)
Application exception: Hotmail
Action for application exceptions: Alert
Definition of file exceptions: -
Change to be made: Add an exception for the Hotmail application, with the action Alert.
7.3 Antivirus and Advanced Threat Protection profile deletion request
Specify the rule to be deleted.
Sample deletion request:
Profile to be deleted: Antivirus
Return to the selection Subjects of change.
7.4 Anti-Spyware profile request
With an antivirus request, you can also order new rules, profiles and user messages for the Anti-Spyware service or change or delete such rules, profiles and user messages.
The figure below presents an Anti-Spyware profile and describes the specifications to be made.

Figure. Anti-Spyware profile.
Definition of profile name (Name)
Specify a name for the profile. The profile name will be used in the policy’s profile definition.
Definition of rule name (Rule Name)
Give a name to the rule.
Definition of scanned threats (Threat Name)
Specify which threats will be scanned for. The default setting is all threats (any). A list of threats is available at https://threatvault.paloaltonetworks.com/ . Please note: this is a rule-name-specific specification.
Definition of category
Specify the categories of traffic that will be scanned. The options are: Any (all, default setting), Adware, Backdoor, Botnet, Browser-hijack, Data-theft, Keylogger, Net-worm
p2p-communication and Spyware. Please note: this is a rule-name-specific specification.
Level of severity (Severity)
Specify the severity of traffic that will be scanned. The options are: Any, critical, high, medium, low and informational. Please note: this is a rule-name-specific specification.
Definition of action (Action)
Specify what action will be taken for traffic of a level of severity that initiates scanning. The options are: Alert, Block (default) and Allow. Please note: this is a rule-name-specific specification.
Definition of packet scanning (Packet Capture)
Specify whether or not a packet will be scanned. The available alternatives are: Yes or No.
Definition of DNS query blocking (DNS Action)
Specify whether DNS queries to known malware domains will be blocked or not. The available alternatives are: Yes (default) or No. This is a profile-specific specification.
Definition of DNS packet scanning (DNS Packet Capture)
Specify whether or not a blocked packet will be scanned. The available alternatives are: Yes (default) or No. This is a profile-specific specification.
Definition of Anti-Spyware exceptions
Specify any threats that will not be scanned. This is a profile-specific specification. A list of threats is available at https://threatvault.paloaltonetworks.com/.
Definition of action for application exceptions (Action)
Specify the action taken for threats for which an exception has been set in the rules. The available alternatives are: Alert, Block (default) and Allow.
Sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample Anti-Spyware profile request
Profile name: Anti-Spyware
Rule name: Critical-low
Scanned threats: Any (all)
Scanned categories: Any (all)
Level of severity: Critical, High, Medium, Low
Action for scanned levels of severity: Block
Packet scanning: Yes
Block DNS queries to malware domains: Yes
DNS packet scanning: Yes
Definition of threat exceptions: -
Action for threat exceptions: -
7.5 Anti-Spyware profile change request
Specify the profile to be changed and the change to be made.
Sample change request
Profile name: Anti-Spyware
Rule name: Critical-Medium
Scanned threats: Any (all)
Scanned categories: Any (all)
Level of severity: Critical, High, Medium
Action for scanned levels of severity: Block
Packet scanning: Yes
Block DNS queries to malware domains: Yes
DNS packet scanning: Yes
Definition of threat exceptions: -
Action for threat exceptions: -
Change to be made: Change the rule name to Critical-medium and levels of severity to Critical, High and Medium
7.6 Anti-Spyware profile deletion request
Specify the rule to be deleted.
Sample deletion request:
Profile to be deleted: Anti-Spyware
Return to the selection Subjects of change.
7.7 Antivirus/Anti-spyware user message
request
The user receives a user message if any viruses detected.

Figure. Antivirus download blocked.
Message name
Give a name to the message.
Message content
Specify the content of the message. The contents of the message can include the name of the file that the user attempted to download.
Saving a rule and sending a request for implementation
When you have made the specifications, select ‘Send request’ or, to add new changes, ‘Add change’. When all the necessary definitions have been made, press ‘Send request’, and the request will be submitted to Telia for implementation.
Sample user message request
Message name: Antivirus block message
Message content: Download of the virus has been blocked in accordance with company policy. Please contact your system administrator if you believe this is in error.
7.8 Antivirus/Anti-Spyware user message change request
Specify the message to be changed and the change to be made.
Sample user message change request
Message name: Antivirus block message
Message content: Download of the virus has been blocked in accordance with company policy. Please contact your system administrator if you believe this is in error.
Change to be made: Change the user message logo. The logo is in the file attached to the request.
7.9 Antivirus/Anti-Spyware user message deletion request
Specify the user message to be deleted.
Sample user message deletion request
Name of the message to be deleted: Antivirus block message
Return to the selection Subjects of change.
8
Intrusion
Prevention
The Intrusion Prevention functionality scans active connections for potential intrusion and attack attempts, such as network worms, Trojans, applications sending usage data without authorisation, and targeted attacks towards vulnerable applications.
An Intrusion Prevention request can be used to order new scanning profiles or change or delete such profiles.
8.1 Intrusion Prevention profile request
The figure below presents a profile scan and descriptions of the settings that can be made in the fields.

Figure. Intrusion Prevention profile request.
Definition of profile name (Name)
Specify a name for the profile. The profile name will be used in the policy’s profile definition. Several rules can be defined for each profile.
Definition of rule name (Rule Name)
Give a name to the rule.
Definition of the names of scanned threats (Threat Name)
Specify the name of the threat being scanned for. The default setting is all threats (any). A list of threats is available at https://threatvault.paloaltonetworks.com/. Please note: this is a rule-name-specific specification.
Definition of scanned device type (Host Type)
Specify whether traffic to clients, servers or both will be scanned. Please note: this is a rule-name-specific specification.
Definition of level of severity (Severity)
Specify the severity of traffic that will be scanned. The options are: Any, Critical, High, Medium, Low and Informational. Please note: this is a rule-name-specific specification.
Definition of action for levels of severity that trigger scanning (Action)
Specify what action will be taken for traffic of a level of severity that initiates scanning. The options are: Alert, Block (default) and Allow. Please note: this is a rule-name-specific specification.
Definition of packet scanning (Packet Capture)
Specify whether packets triggering a rule will be scanned or not. The available alternatives are: Yes or No. Please note: this is a rule-name-specific specification.
Sample Intrusion Prevention profile request
Profile name: Intrusion Prevention
Rule name: Critical-low
Scanned threats: Any (all)
Scanned device type: Client and Server
Level of severity: Critical, High, Medium, Low
Action for level of severity: Block
Packet scanning: Yes
8.2 Intrusion Prevention profile change request
Specify the profile to be changed and the change to be made.
Sample change request
Profile name: Intrusion Prevention
Rule name: Critical-Medium
Scanned threats: Any (all)
Scanned device type: Client and Server
Level of severity: Critical, High, Medium
Action for level of severity: Block
Packet scanning: Yes
Change to be made: Change the specification of severity-level-based scanning. Rule name Critical-Medium, delete Low from the levels of severity.
8.3 Intrusion Prevention profile deletion request
Specify the profile to be deleted.
Sample deletion request:
Profile to be deleted: Intrusion Prevention
Return to the selection Subjects of change.
9
User
awareness
The functionality enables the identification of users, user groups and devices to be identified, restriction of access, and the implementation of the security policy on the basis of identity and user group. The introduction of the functionality requires the integration of the system with the customer’s user directory. The customer is responsible for the maintenance and management of the user directory.
With a user identification request, you can order changes to the IP addresses of the domain controllers, to the domain name or to the user ID (username, password) of the service account.
If the request relates to the user identification functionality, our specialist will contact you before the delivery if necessary.
Sample change to the user identification functionality:
Change the Secondary AD's IP address 10.10.10.10 to 10.10.10.11. The Domain Admin password will remain unchanged.
Return to the selection Subjects of change.
10
Access
right request
An access right request can be used to order rights for the customer’s administration personnel, authorising the centralised management of the service and viewing the rules of the service and other configuration and log information. Usernames will be created for users of the SurfManager as requested.
The request must indicate the username and public IP address from which the user’s connection will be opened. The password and mobile phone number for SMS identification are the same as those used for SurfManager. The username must have access rights to the security reporting view in SurfManager.
The tools will only function if a connection to the administration servers has been opened in the customer’s own firewall. A firewall opening will not be made unless specifically requested in the change request. We recommend that the customer should make the address change in its own firewall so that the connections of all users will be displayed under a single NAT address. If the NAT address changes at some point, this will require an access right change request stating the new address.
Sample access right change:
A user ID for the client is created for the user abc12345. The user’s IP address is 1.1.1.1. The password will be sent by SMS when the request has been implemented.
Return to the selection Subjects of change.
/11
Expert
services
With an expert services request, you can order remote specialist work related to the service.
The deliverability and schedule of the work is confirmed separately. Examples of specialist work include firewall-related reports, data collection and requests for information.
Example of specialist work
Find out which rules have not been used during the past two months. These rules should be disabled and deleted after approval.
Return to the selection Subjects of change.
12
Stand-by/On-call
With a stand-by/on-call request, you can order a member of the production personnel to be on stand-by or on call.
Stand-by means that a specialist is reserved for a certain time, for example, if a specialist is needed to make firewall openings during a network change.
Work performed during stand-by is invoiced according to the price list for specialist work. Stand-by requests must be made at least two working days in advance. Please note: the delivery time for the order must be ”scheduled”. Telia will confirm the stand-by service and give the specialist’s contact details. In the service request field, you should enter the dates, times and reason for the stand-by requirement.
Sample stand-by request
We will need a specialist on stand-by for Saturday this week, from 12:00 to 16:00. We will make routing changes in our network, and these may affect the firewall.
Return to the selection Subjects of change.
13
Reporting
and logs
With a reporting request, you can order more detailed reports on the traffic that has passed through the information security services. You can also request changes to the settings of reporting, such as the reporting interval.
Sample reporting request
Provide a report on traffic to the address 10.10.10.10 during the past week.
Return to the selection Subjects of change.
14
Other
configuration change
With an other configuration change request, you can order small changes to the information security device, such as changes to its interface settings.
Return to the selection Subjects of change.